Search this site

Improve Your Security Posture
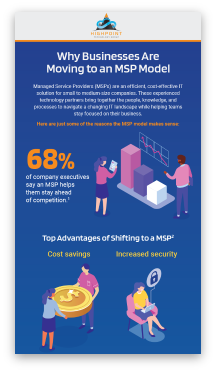
Technology is always changing, from the emergence of the Internet of Things (IoT) to the preference for Software as a Service (SaaS) over custom internal applications. The threat landscape also evolves as a result of technological advancements.
However, many businesses make technology changes without the assistance of IT, information security, risk, or procurement experts. At HighPoint Technology Group, we want to help you improve your security posture to reduce the chance of a breach situation.
However, many businesses make technology changes without the assistance of IT, information security, risk, or procurement experts. At HighPoint Technology Group, we want to help you improve your security posture to reduce the chance of a breach situation.
Discover the HighPoint Difference
Enhanced Security
Enjoy peace of mind knowing that your systems and data are shielded from cutting-edge security risks, such as phishing and ransomware.
Round-the-Clock Support
Gain access to 24/7 IT support for any device or issue to reduce the chances of downtime and network failures.

HighPoint Magic Portal
See into the future with individualized strategic recommendations, costs, dates, and priorities, as well as the option to group projects together to receive a discount.
Our Cyber Security Services

Managed Detection and Response
We provide organizations with access to skilled analysts and advanced detection capabilities, ensuring that potential threats are identified, investigated, and addressed efficiently.
Skilled resource gap
Some threats can’t be clearly defined as good or bad by even the best technology. MDR services can be a cost-effective way to access the necessary detection & response skills and resources without having to recruit, train, and retain internal talent.
Alert fatigue
The number of alerts generated by security tools means that the humans involved fail to spot the important alerts among the noise. MDR services lend a helping hand to review, validate, and address alerts.
Time limitations
Investigating alerts and hunting for undetected threats are time consuming. It takes additional time to respond effectively to a confirmed threat. With IT and security resources stretched thin, some organizations prefer to outsource these tasks, freeing up staff for other priorities.
24/7 coverage
Few organizations have the in-house personnel to monitor for threats around-the-clock.

Managed Cybersecurity – Powered by Sophos
24/7 threat detection and response
Sophos MDR is a fully managed 24/7 service delivered by experts who detect and respond to cyberattacks targeting your computers, servers, networks, cloud workloads, email accounts, backups, and more.Why Sophos MDR?
Integration and protection
Sophos offers a unique combination of integrations for the highest return on investment and leading native technology for the best proactive protection. Competitors typically offer one or the other, but not both.
- Integrations – Sophos MDR integrates with the endpoint, network, firewall, email, cloud, and identity solutions an organization is already using – both Sophos and third-party. This means that HTG customers do not need to rip and replace to benefit from Sophos MDR, while enabling them to get more detections and better returns from their existing security investments.
- Strong protection – Sophos’ combination of industry leading technology, multi-discipline human expertise, and breadth of experience enables Sophos MDR to deliver accelerated detection and response with an average resolution time of 38 minutes.
Instant SOC
No need for an in-house Security Operations Center (SOC)
- Fully managed response — With HTG’s oversight, Sophos’ response team can engage fully and take control of a threat, from detection through investigation to neutralization. Many other MDR services only notify customers of attacks or suspicious activities or require a response retainer for a limited number of response hours.
- Flexible response modes — The MDR Complete response team can adapt its engagement depending on customer requirements. This means peace of mind for customers who know that they will get the help they need without any unwanted interference.
- Robust lead-driven and leadless threat hunting — Sophos threat hunters use the latest intelligence and their expertise to proactively hunt for and validate potential threats.
Network Detection and Response (NDR)
Sophos NDR brings in full visibility of network activity, leaving threat actors nowhere to hide. This visibility adds context and depth to investigations leading to faster resolutions and more accurate route cause analysis.

Endpoint Protection
Defend endpoints against increasingly sophisticated attacks by leveraging our managed endpoint protection services, such as:
Endpoint antivirus protection
Design, configure, and deploy antivirus policies with our proven strategies and approach.
Data loss prevention
Protect against malicious or accidental misuse or loss of sensitive information by enacting policies aligned with regulatory compliance.
Endpoint encryption
Leverage the most recent encryption technologies to protect against device loss or theft.
Managed endpoint security
Keep constant state operations via monitoring, upkeep, and routine updates from trained security analysts along with a centralized management console.

Vulnerability Assessments
Complete the first step in understanding your organization’s cybersecurity position by identifying any existing vulnerabilities with our vulnerability scan. Using one or more “scanning” tools, we analyze your entire infrastructure to find any potential technical vulnerabilities. This is done to:
- Match critical vulnerabilities with critical assets
- Generate a list of patches or other solutions to apply to those vulnerabilities
- Identify any false positives or false negatives
- Improve your cyber security posture, both internally and externally
- Save internal time and effort without interruptions to your normal business activities
- Find areas where your existing security solutions might not be optimized to reach their potential

Penetration Testing
Build your organization’s cyber security confidence with our penetration testing services. Penetration testing (or pen testing) is performing a simulated attack against your organization to uncover any flaws in your business’ cyber security infrastructure. This is a highly efficient way to:
- Confirm the performance of your detection and monitoring systems
- Enhance your comprehension of layered security exploitation
- Discover just how vulnerabilities can be employed to exploit your system
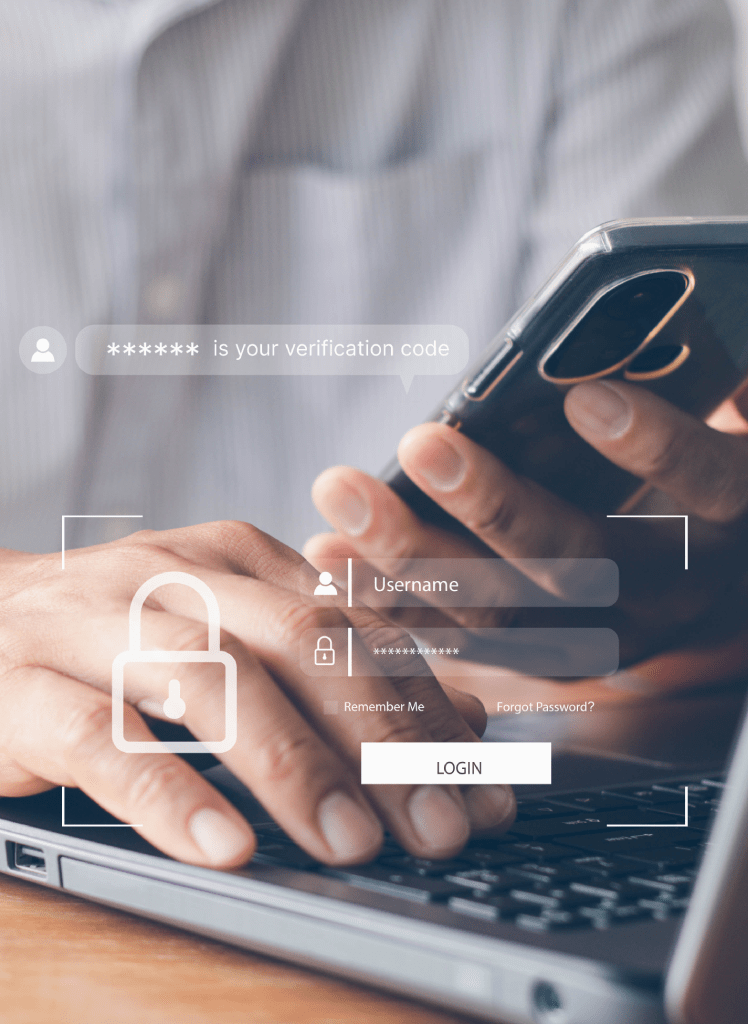
Directory Services and Multi-Factor Authentication
Directory services are a critical component of your IT security program, and our team makes it simpler and easier for you to access the apps and data you need – anytime, anywhere. Key features and capabilities include unified access for:
IT managers
Save hours every week on access management operations like provisioning, password reset, and offboarding with automated workflows and self-service password reset for users.
IT executives
Accelerate strategic initiatives, including cloud migration and application deployment, while gaining operational efficiency, reducing costs, and improving employees’ digital experiences.
Security professionals
Protect all apps with a secure single sign-on (SSO) portal and enforce security with contextual access policies and adaptive multi-factor authentication (MFA).
Everyone
Simplify access for every user, including full-time employees, contractors, partners, and even customers, and every app with an intuitive SSO portal.

Enterprise Patching
Free up your resources to innovate and speed up the digital transformation process with our enterprise patch management program. Not evolving or moving too slowly puts your organization at risk of disruption, losing market share, or worse. Patch management:
- Fixes problems with software and firmware’s security and functioning
- Reduces exploitation opportunities by addressing software defect vulnerabilities
- Can add new features to software and firmware
- Ensures you meet all compliance requirements and laws so that the regulatory organizations don’t impose financial penalties







Frequently Asked Questions
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod?
Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit.
Diagnostics techniques & programmation
Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit.
Diagnostics techniques & programmation
Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit.
Diagnostics techniques & programmation
Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit.
Get a Free Technology Assessment
Cyberattacks and downtime cost you money and endanger your company. Uncover any vulnerabilities with an audit of your IT network.